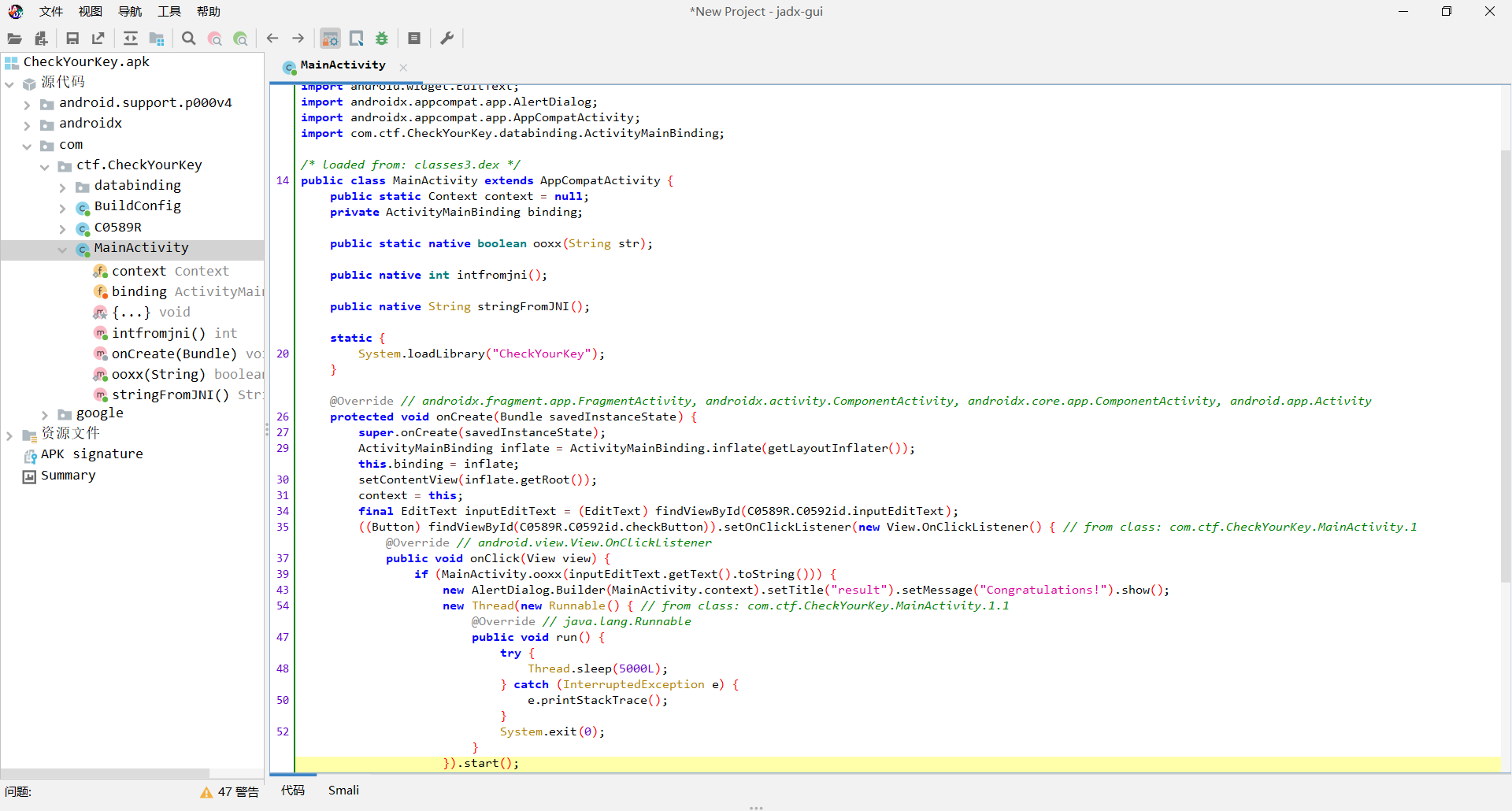
2022RCTF RE 部分wp CheckYourKey 逆向签到题,apk没什么好说的,就是调用so库里面的ooxx文件对输入进行检查,直接看so库
在函数栏中直接搜索ooxx,定位到
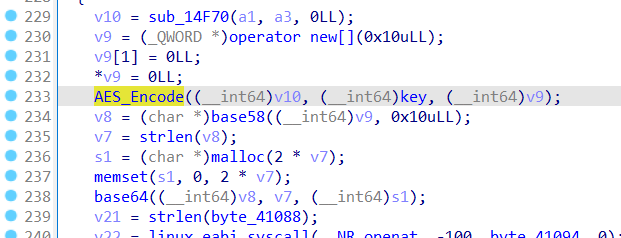
Java_com_ctf_CheckYourKey_MainActivity_ooxx函数 定位到这里
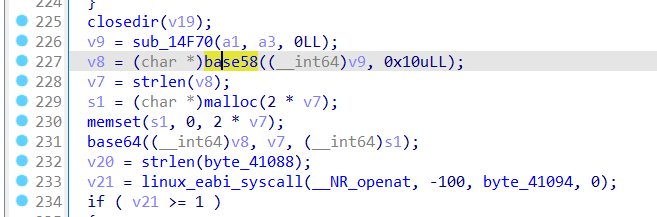
第227行和第231行的函数分别是base58,base64加密
base58函数 可以看到这里的(138 * a2 / 0x64) + 2 和 div(quot_low + (v14[–v8] << 8), 58),所以猜测是base58加密
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 unsigned __int8 *__fastcall sub_F7DC (__int64 a1, unsigned __int64 a2) unsigned __int64 v2; bool v5; unsigned __int64 v6; div_t v7; unsigned __int64 v8; unsigned __int64 v9; int quot_low; unsigned __int64 v11; unsigned __int64 j; unsigned __int64 v13; unsigned __int8 *v14; unsigned __int64 i; for ( i = 0LL ; !*(_BYTE *)(a1 + i); ++i )unsigned __int8 *)malloc ((unsigned int )(138 * a2 / 0x64 ) + 2 );memset (v14, 0 , 138 * a2 / 0x64 + 2 );for ( j = 0LL ; j < i; ++j )0LL ;while ( j < a2 )unsigned __int8 *)(a1 + v3);0LL ;138 * a2 / 0x64 + 1 ;while ( 1 )if ( quot_low || (v5 = 0 , v9 < v11) )0 ;if ( !v5 )break ;8 ), 58 );138 * a2 / 0x64 + 1 - v11 - i;while ( v13 < i + v11 )if ( v6 )0 ;return v14;
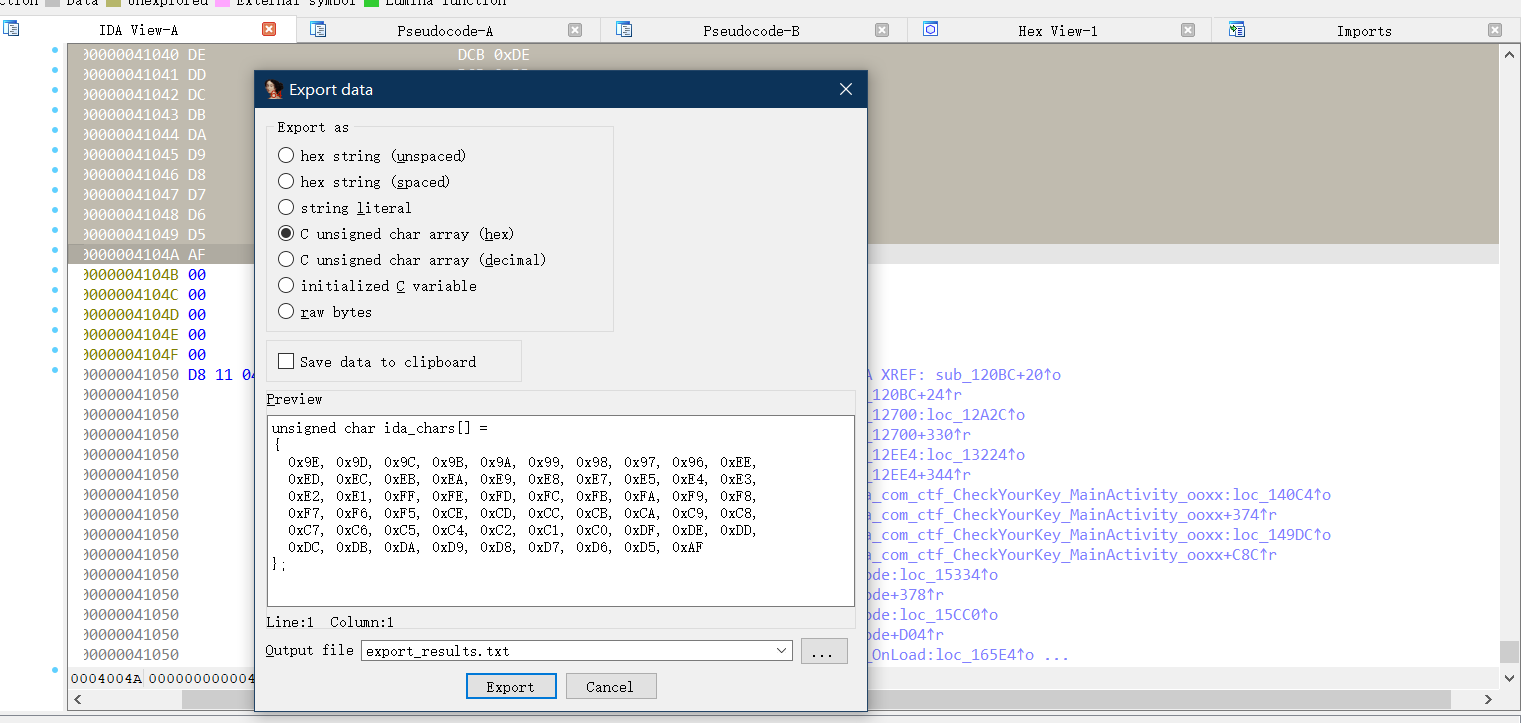
可以找到长度为58的表,但是内容不太对,X找交叉引用
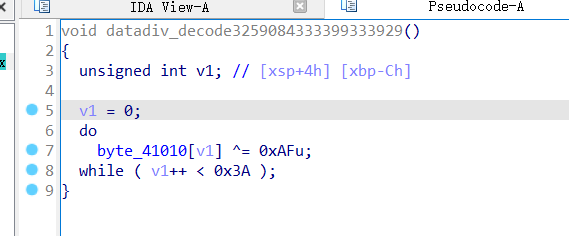
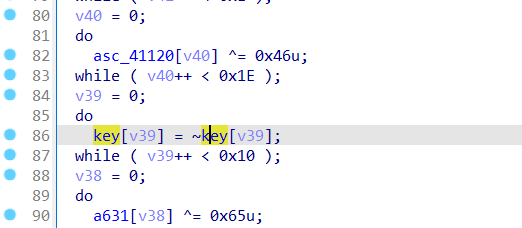
找到这里有异或的操作
直接上脚本测试一下,得到了base58的码表,确定这里是base58加密
1 2 3 4 5 6 7 8 9 10 11 12 13 14 byte_41010 = [0x9E , 0x9D , 0x9C , 0x9B , 0x9A , 0x99 , 0x98 , 0x97 , 0x96 , 0xEE , 0xED , 0xEC , 0xEB , 0xEA , 0xE9 , 0xE8 , 0xE7 , 0xE5 , 0xE4 , 0xE3 , 0xE2 , 0xE1 , 0xFF , 0xFE , 0xFD , 0xFC , 0xFB , 0xFA , 0xF9 , 0xF8 , 0xF7 , 0xF6 , 0xF5 , 0xCE , 0xCD , 0xCC , 0xCB , 0xCA , 0xC9 , 0xC8 , 0xC7 , 0xC6 , 0xC5 , 0xC4 , 0xC2 , 0xC1 , 0xC0 , 0xDF , 0xDE , 0xDD , 0xDC , 0xDB , 0xDA , 0xD9 , 0xD8 , 0xD7 , 0xD6 , 0xD5 , 0xAF , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 ]'' for i in range (58 ):0xAF chr (byte_41010[i])print (table)
base64函数 这里的就很容易看出来是base64了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 __int64 __fastcall sub_13788 (__int64 a1, unsigned int a2, __int64 a3) unsigned __int8 v13; unsigned __int8 v14; unsigned int v15; unsigned int v16; unsigned int v17; unsigned int v18; unsigned int i; int v20; 0 ;0 ;0 ;for ( i = 0 ; i < a2; ++i )if ( v20 )if ( v20 == 1 )2 ;16 * (v13 & 3 )) | ((int )v14 >> 4 ) & 0xF ];else 0 ;1 ;4 * (v13 & 0xF )) | ((int )v14 >> 6 ) & 3 ];1 ;0x3F ];else 1 ;int )v14 >> 2 ) & 0x3F ];if ( v20 == 1 )1 ;16 * (v13 & 3 )];61 ;1 ;61 ;else if ( v20 == 2 )1 ;4 * (v13 & 0xF )];1 ;61 ;0 ;return v15;
可以看出来是换表的base64加密
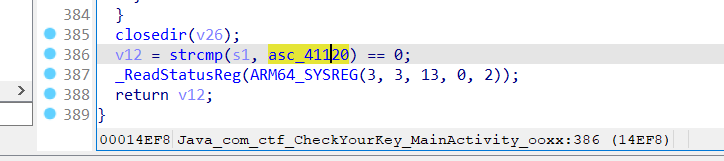
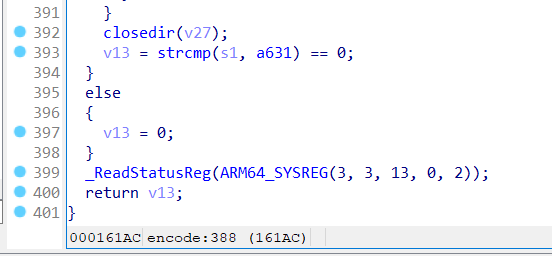
在该函数的最后找到strcmp函数
可以知道最后的密文就是asc_41120,x交叉引用找到了另外的调用
先异或后解密,但是结果不对,猜测有其他的加密
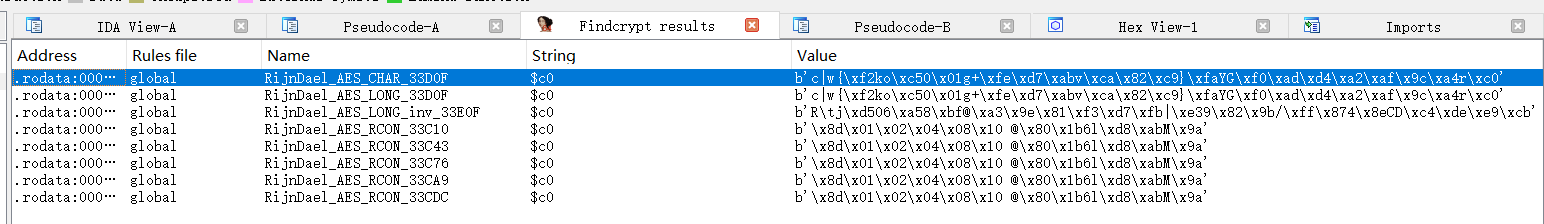
利用findcrypt找到了AES加密,直接定位到该函数
sub_14FC0函数 该函数的整体逻辑和上面的ooxx函数十分相似,所以直接定位到
整体的加密逻辑就是先AES后base58最后base64
AES的key刚好就是该函数的第二个参数,直接提取出来
1 2 3 4 5 6 7 unsigned char key[] =0x98 , 0x90 , 0x90 , 0x9B , 0x93 , 0x8A , 0x9C , 0x94 , 0x8C , 0x92 , 0x9E , 0x8D , 0x8B , 0x92 , 0x9E , 0x91 , 0xFF , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00
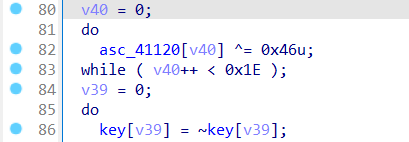
刚才在找asc_41120的交叉引用是定位到了一个函数,在那里同时也找到了key的处理,直接输出得到key
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 #include <stdio.h> #include <stdlib.h> #include <iostream> #define _BYTE unsigned char int main () unsigned char key[] =0x98 , 0x90 , 0x90 , 0x9B , 0x93 , 0x8A , 0x9C , 0x94 , 0x8C , 0x92 ,0x9E , 0x8D , 0x8B , 0x92 , 0x9E , 0x91 , 0xFF , 0x00 , 0x00 , 0x00 ,0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 ,0x00 , 0x00 for (int i = 0 ; i < 32 ; i++)printf ("%c" , (_BYTE)~key[i]);return 0 ;
最后比较的密文也不一样,但是同样给要先经过异或处理
最后是从NU1L那里学来的python脚本,也可以用cyberchef直接解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 import base64import binasciifrom Crypto.Cipher import AES'123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz' def base58decode (s ): 0 for c in s:58 + b58.find(c)return result"+/EFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789ABCD" "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" "SVTsfWzSYGPWdYXodVbvbni6doHzSi==" '' '' '' for i in range (len (enflag)):print (enflag1)print (hex (base58decode("A4juLPXCTmefm6mfX8naqB" )))hex (base58decode("A4juLPXCTmefm6mfX8naqB" ))[2 :].encode("utf8" ))list (b'goodlucksmartman' )bytes (key), mode)bytes (data))print (flag)
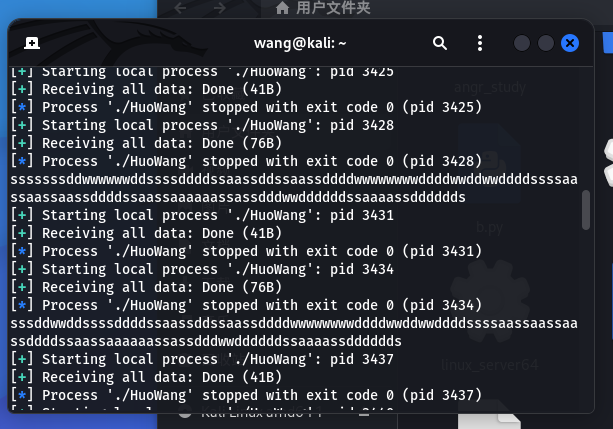
HuoWang 一个迷宫题
程序的符号表是被去除了,但是群里大哥看出来是unicorn写的了
使用bandiff恢复一下符号表,顺便搜索了一下各个函数的功能
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 int __cdecl main (int argc, const char **argv, const char **envp) int result; int v5; int i; int len; int v8; 3 ]; int v11; char input[264 ]; unsigned __int64 v13; 0x28 u);scanf ((__int64)"%s" , input);strlen ();0xFFFFF ;for ( i = 0 ; i <= 6 ; ++i )4u , 8 , &uc); 0x200000 LL, 7u );0LL , 0x100000 LL, 7u );1 ] = 0LL ;2 ] = 0LL ;0 ;0x7AA8 uLL);30 , (__int64)&v5); 2 , (__int64)sub_401FC5, 0LL , 1LL , 0LL , 0x2BB , (int )argv);0x400119 LL, 0x40016A LL, 0LL , 0LL );0x40016A LL, &qword_4000D8, 0LL , 0LL );0x40016A LL, v3);if ( check1 && check2 )puts ((__int64)"GrandFather Dao, I've made it!(ohhhhh. The flag is RCTF{(md5(your input))}." );else if ( check1 || check2 )puts ((__int64)"Mom, I really can't tell the difference!" );else puts ((__int64)"CTF is fun! Jie Jie Jie" );0 ;if ( __readfsqword(0x28 u) != v13 )return result;
主要的迷宫还是在maze函数中
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 __int64 __fastcall maze (__int64 a1, __int64 a2, int a3) int v4; int v5; unsigned int i; 0 ;1 ;for ( i = 0 ; ; ++i )if ( (int )i >= a3 )break ;unsigned __int8 *)((int )i + a2);if ( (_DWORD)result == 'w' )if ( !v4 )return result;unsigned __int8 *)(a1 + 24LL * v4 - 24 + v5);if ( (_BYTE)result != ' ' )return result;else if ( *(unsigned __int8 *)((int )i + a2) > 0x77 u )goto LABEL_20;if ( (_DWORD)result == 's' )unsigned __int8 *)(a1 + 24 * (v4 + 1LL ) + v5);if ( (_BYTE)result != ' ' )return result;else if ( *(unsigned __int8 *)((int )i + a2) > 0x73 u )goto LABEL_20;if ( (_DWORD)result == 'a' )if ( !v5 )return result;unsigned __int8 *)(a1 + 24LL * v4 + v5 - 1 );if ( (_BYTE)result != ' ' )return result;else if ( (_DWORD)result != 'd' )-1 );unsigned __int8 *)(a1 + 24LL * v4 + v5 + 1 );if ( (_BYTE)result != ' ' )return result;if ( v4 == 22 && v5 == 21 )1 ;return result;
其中a1是
可以得知我们要做的就是从左上角走到右下角,wsad分别对应上下左右,需要找到最短路径
主要方法还是遍历破解,来自Arr3stY0u战队的wp(orz)
2022 RCTF writeup by Arr3stY0u (qq.com)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 from pwn import *"0S000000000000000000000" ,"01011111011111110111110" ,"01010101000101000101010" ,"01110101111101011101010" ,"01010100000000010100010" ,"01010111110111110101110" ,"01010000010101000001010" ,"01110101110111111111010" ,"00010101000101000100010" ,"01110101110101011101110" ,"01000100010101011100010" ,"01110101110101011111010" ,"01010101000101000001010" ,"01011101111111110111010" ,"01000000000001000101010" ,"01110111110111111101010" ,"01000000000100000000010" ,"01110010001101111111010" ,"01110100001001000001010" ,"01110101101111011111010" ,"01010101010000010000010" ,"01111111011111011111110" ,"000000000000000000000E0" def dfs_solve_maze (map , x, y, walks, path, allpathif x < 0 or x >= 23 :return allpathif y < 0 or y >= 23 :return allpathif (x, y) in walks:return allpathif map [y][x] not in 'S1E' :return allpathif map [y][x] == 'E' :return allpathmap , x-1 , y, new_walks, path+'a' , allpath)map , x+1 , y, new_walks, path+'d' , allpath)map , x, y-1 , new_walks, path+'w' , allpath)map , x, y+1 , new_walks, path+'s' , allpath)return allpath1 , 0 , set (), '' , set ())for p in allpath:"./HuoWang" )if b"flag" in out:print (p)
通过dfs遍历所有的情况
然后md5加密得到flag
1 2 3 4 5 6 7 8 import hashlib"sssddwwddssssddddssaassddssaassddddwwwwwwwwddddwwddwwddddssssaassaassaassddddssaassaaaaaassassdddwwddddddssaaaassdddddds" 'utf-8' ))print ('flag{' ,end='' )print (enc.hexdigest(),end='' )print ('}' )
RTTT 一道有点抽象的rust逆向(rust都抽象)
首先静态分析一下
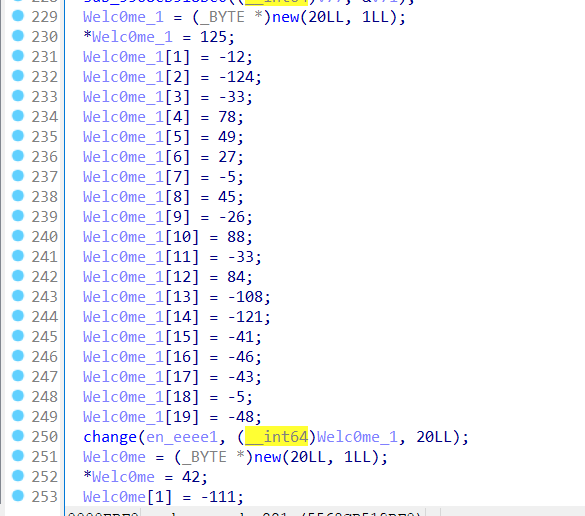
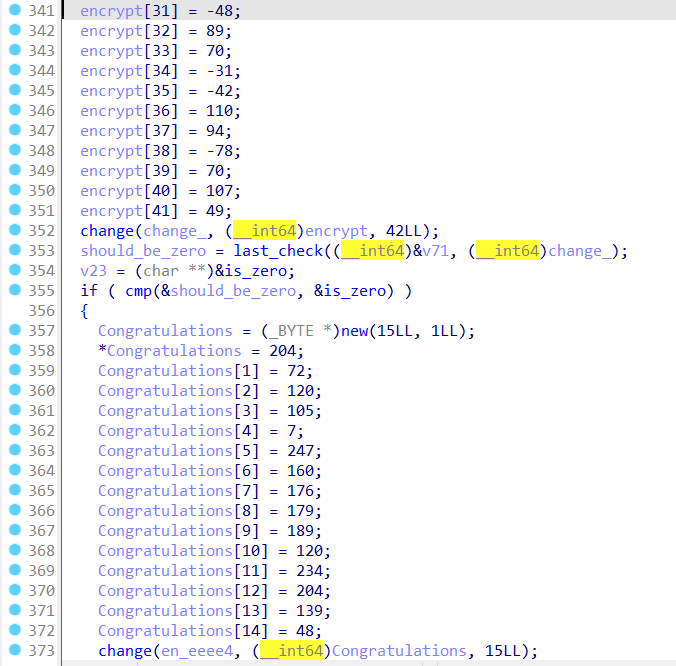
找到了五个很可疑的数组
看到他们后续的操作是异或,直接上手,发现结果就是
1 2 Welc0me to RCTF 2 O22Congratulations
所以猜测congratulations前面的那个数组大概率是密文
直接在左侧搜索memcmp函数,x找交叉引用定位到最后密文做比较的地方
直接开始动调,F8到输入处开始跟踪,然后发现第一个操作是打乱输入顺序
input:RCTF{abcdefghijklmnopqrstuvwxyz0123456789}
打乱后t4u6f2rysRxvoin}dkh3wacgeF1C{9l58Tz7pbq0jm
看F61d大佬们的wp
RCTF 2022 WriteUp By F61d | CTF导航 (ctfiot.com)
得知第二步加密居然是RC4,我是看了两个多小时没看出来,居然只凭借这点信息就能判断出来是RC4,真厉害
借用一下脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 from Crypto.Cipher import ARC4b'Welc0me to RCTF 2O22' )52 , 194 , 101 , 45 , 218 , 198 , 177 , 173 , 71 , 186 , 6 , 169 , 59 , 193 , 204 , 215 , 241 , 41 , 36 , 57 , 42 , 192 , 21 , 2 , 126 , 16 , 102 , 123 , 94 , 234 , 94 , 208 , 89 , 70 , 225 , 214 , 110 , 94 , 178 , 70 , 107 , 49 ]bytes (t1)).decode()print (f)'RCTF{abcdefghijklmnopqrstuvwxyz0123456789}' 't4u6f2rysRxvoin}dkh3wacgeF1C{9l58Tz7pbq0jm' for i in range (len (s2)):'' for i in range (42 )]for i in range (len (f)):print ('' .join(f1))
Web_run wasm逆向, ez_wasm.2 改为 ez_ca.wasm ,ez_wasm.1 改为 ez_wasm.html
然后直接用jeb打开.wasm
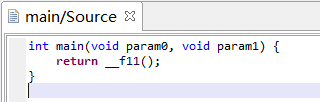
main()
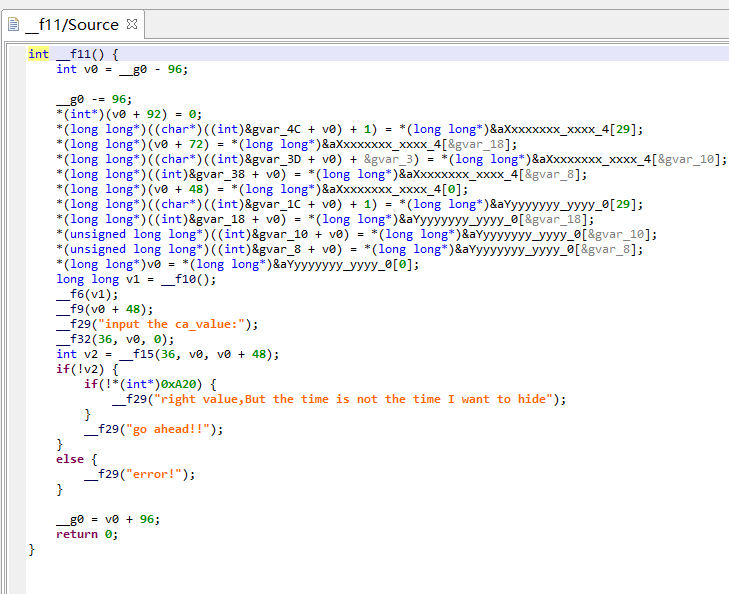
f11()
关键函数主要是f10(), f6(),f9()这三个
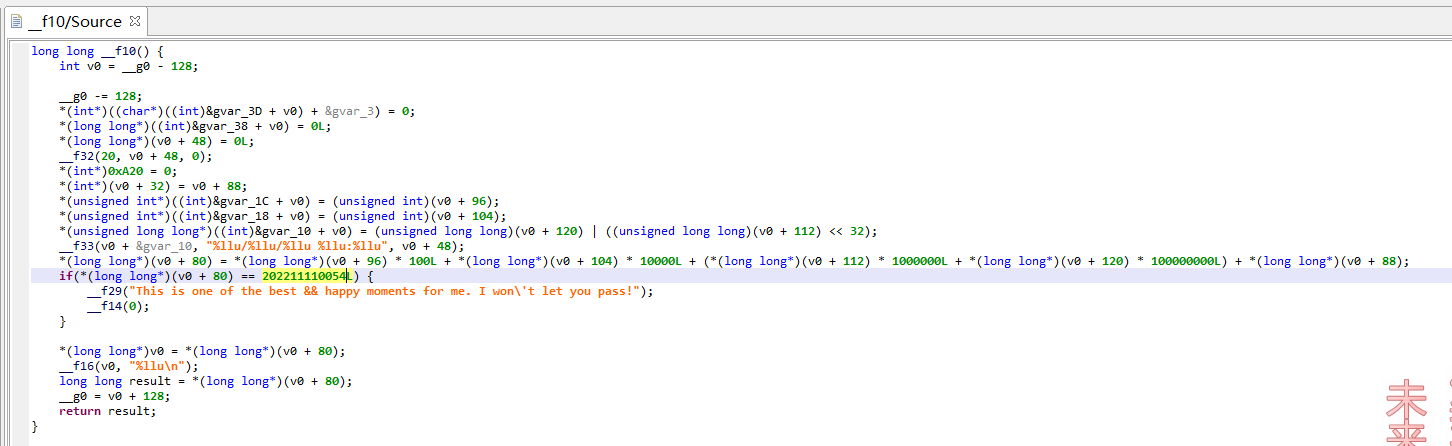
f10()
主要是输入data,格式为xxxx/xx/xx xx:xx,解析成为一个整数
要留意的是202211110054这个数
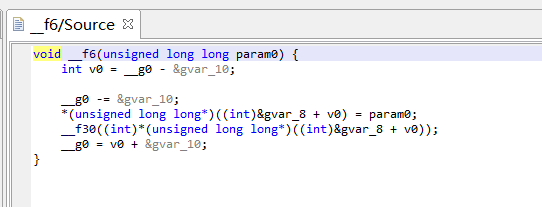
f6()
主要功能就是把f10()返回的result值赋给全局变量
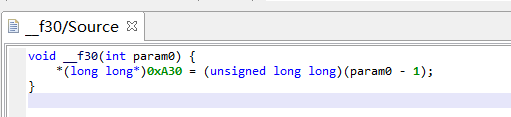
f30() 其中有对0xA30处值的初始化
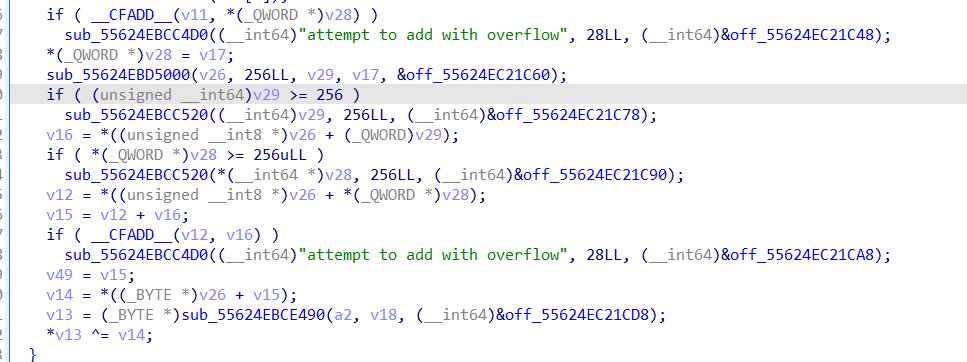
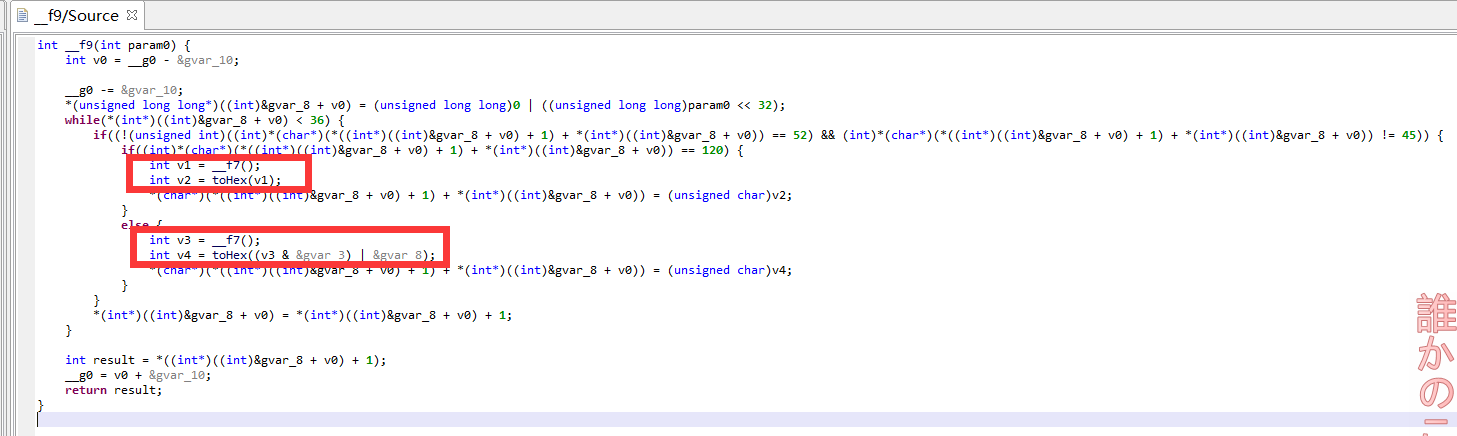
f9() 分情况对这个整数进行加密
具体是”xxxxxxxx-xxxx-4xxx-yxxx-xxxxxxxxxxxx”
红框部分就是主要的加密过程
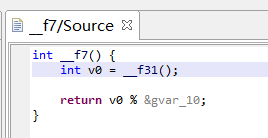
f7()
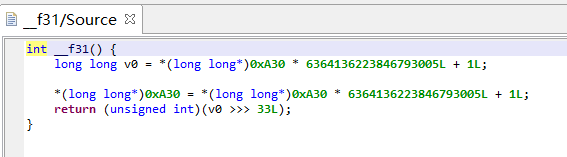
f31()
主要的加密就是f31()的返回值模16,然后按照对应规则转换为16进制
写脚本
由于是复现,所以直接与已知的官方flag进行比较
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 #include <iostream> #include <string> using namespace std;int main () long long magic = 6364136223846793005 ;long long data = 202211110054 ;long long A30 = (int )data - 1 ;"RCTF{40959ea7-26e0-4c9d-8f4a-62faf14ff392}" ;"RCTF{" ;char str[] = "xxxxxxxx-xxxx-4xxx-yxxx-xxxxxxxxxxxx" ;for (int i = 0 ; i < strlen (str); i++) {if (str[i] != '4' && str[i] != '-' ) {long long res = A30 * magic + 1 ;unsigned int v0 = (unsigned int )(res >> 33 );int num = v0 % 16 ;if (str[i] == 'y' ) {3 ) | 8 );if (num >= 0 && num <= 9 ) {'0' ;else {10 + 'a' ;else {'}' ;if (flag == test) {printf ("correct!\n" );return 0 ;