babyre
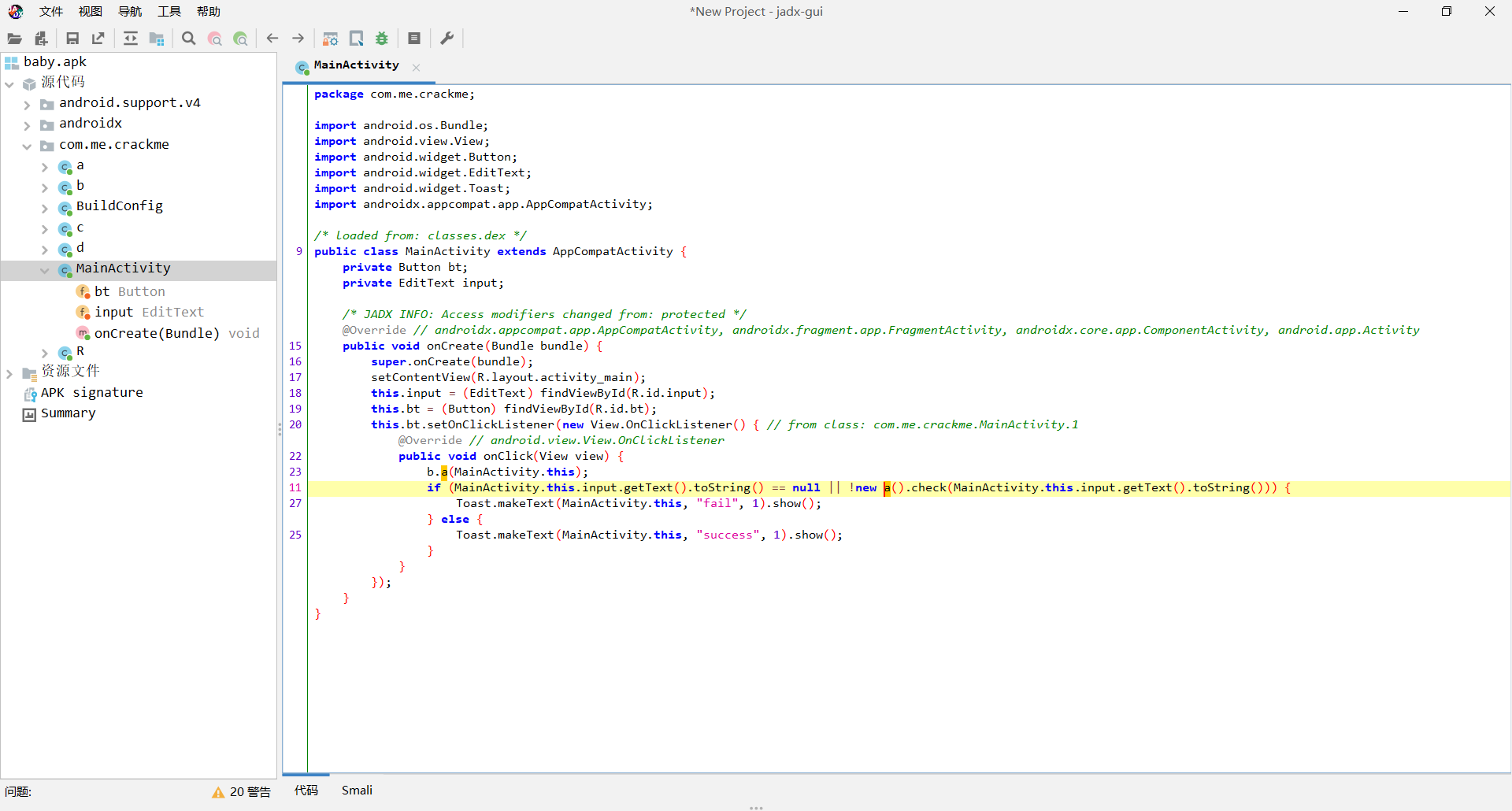
随后是调用了a().check()函数判断输入的是否正确

直接写脚本
1
2
3
4
5
6
7
8
9
10
11
12
| import base64
a = "a214bmVqaXlieHpjaXhuc2p4bm5hc20="
c = base64.b64decode(a.encode("ascii"))
byte = []
for i in range(len(c)):
byte.append(c[i])
byte[i] = (byte[i] >> 3)
byte[i] = (byte[i] ^ 102)
byte[i] = (byte[i] - 10)
byte[i] = chr(byte[i])
print(byte)
|
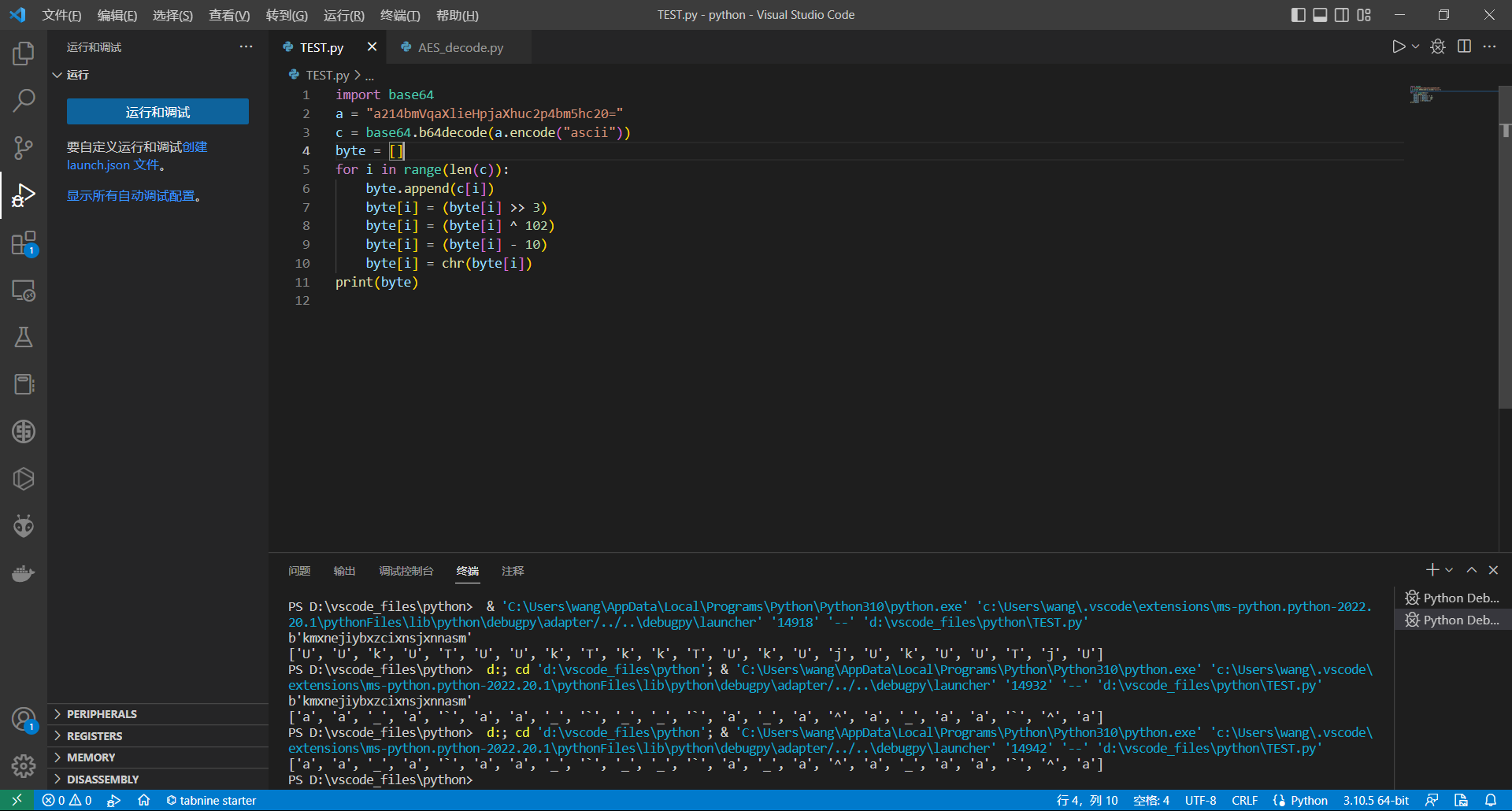
可以看到最后的结果并不正确,所以这个a.check并不是最终的判断函数
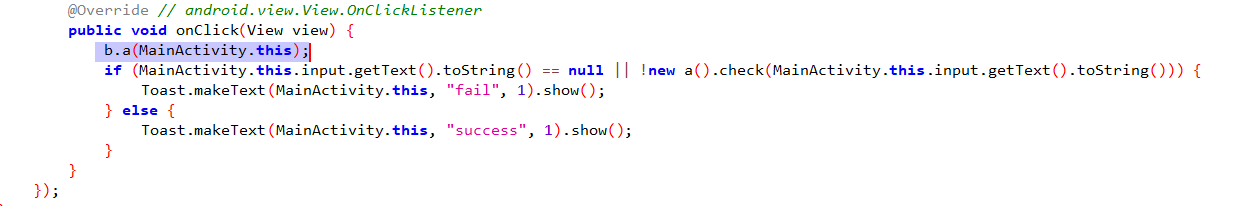
看到在调用a.check之前先是调用了b.a()这个函数,跟进查看
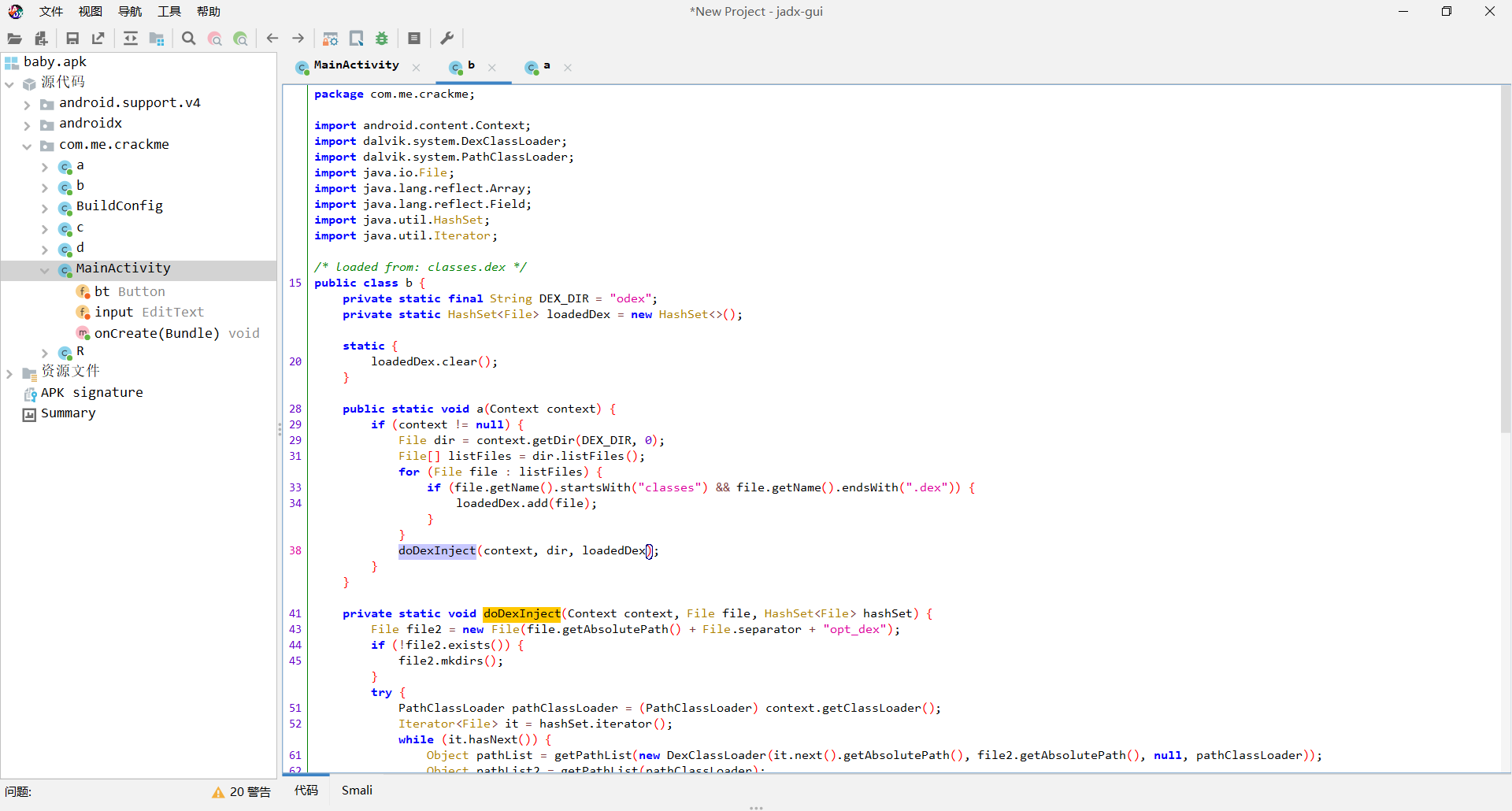
看到有个doDex注入,感觉是有鬼,但是具体找不到在哪里
漫无目的的查看com.me.creackme下的所有类
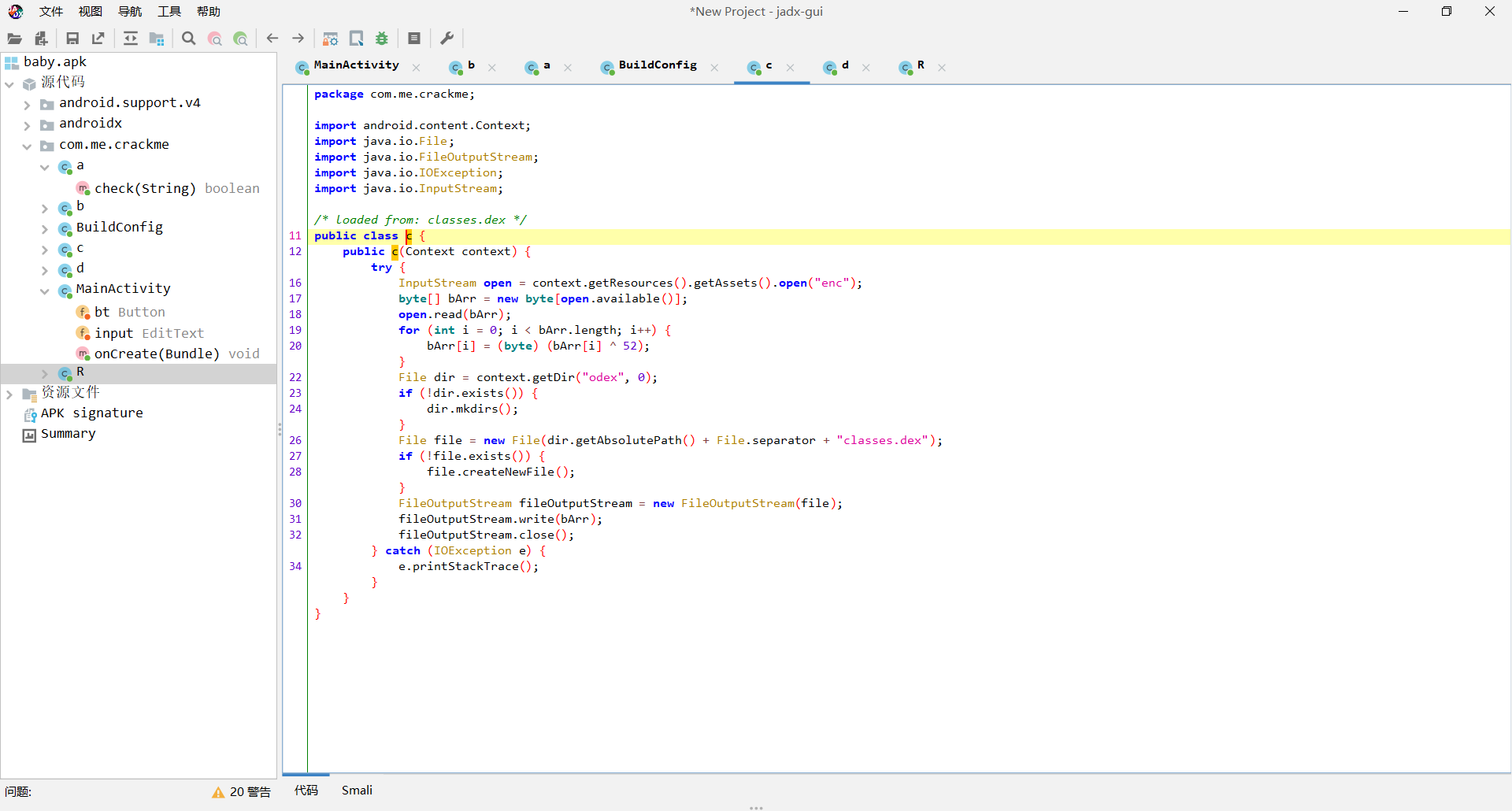
看到C这个类有进行打开enc文件然后进行异或的操作,解压apk找到了这个enc文件
写脚本解密
1
2
3
4
5
6
7
8
9
10
| def decrypt(src_file, dest_file):
with open(src_file, 'rb') as f_src:
with open(dest_file, 'wb') as f_dest:
byte = f_src.read(1)
while byte:
f_dest.write(bytes([byte[0] ^ 52]))
byte = f_src.read(1)
decrypt('enc', 'decrypted.dex')
|
然后用jadx打开在同级目录下生成的decrypted.dex
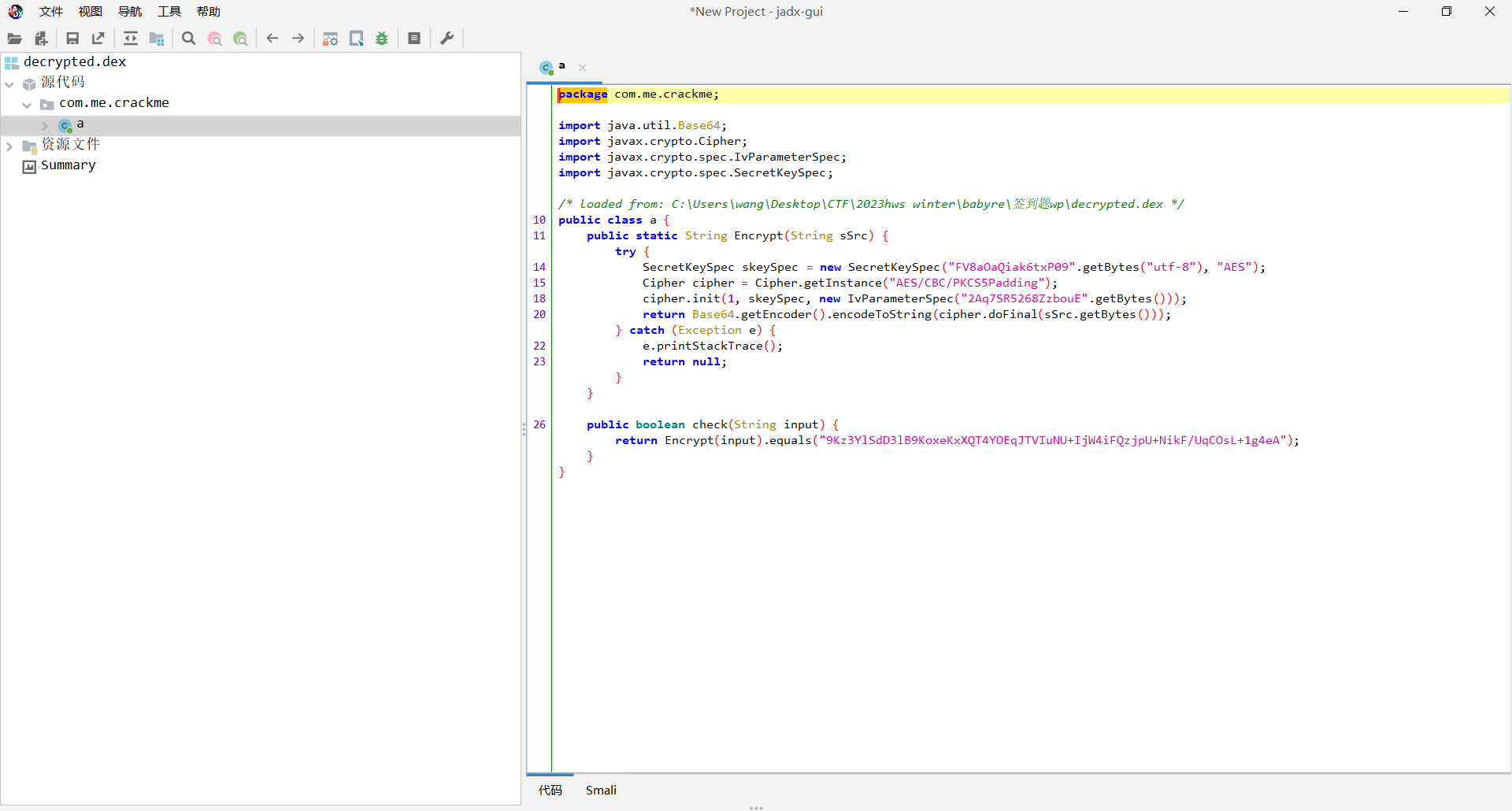
这里是AES加密,而且这个类的名字也是a,猜测是b类中的Dex注入了这个decrypted.dex到原来的文件里,感觉是相当于hook了a类,实际上的a类是这里的AES加密
解密脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| import base64
from Crypto.Cipher import AES
import codecs
def decrypt(key, iv, enc):
cipher = AES.new(key, AES.MODE_CBC, iv)
return cipher.decrypt(enc)
key = b'FV8aOaQiak6txP09'
iv = b'2Aq7SR5268ZzbouE'
enc = base64.b64decode('9Kz3YlSdD3lB9KoxeKxXQT4YOEqJTVIuNU+IjW4iFQzjpU+NikF/UqCOsL+1g4eA')
decrypted = decrypt(key, iv, enc)
print(decrypted.decode())
|
所以最后
flag{076a554cef6742b402d74c1013dadde9}
sound from somewhere
wav文件,用Audacity打开之后发现是波形
经过一番搜索,最终定位到了sstv
下载虚拟声卡,然后Audio Repeater设置
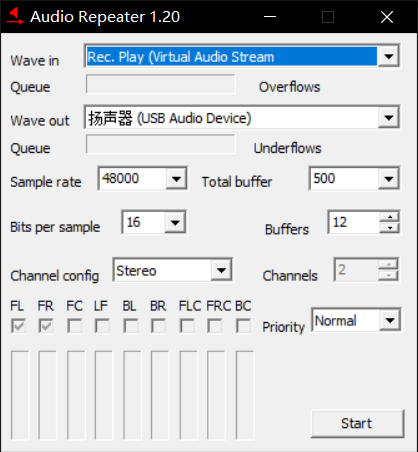
Robot36,然后播放

得到flag

所以flag就是flag{OuTer_Wilds}
easyre
一眼顶针,主要的加密逻辑是XTEA
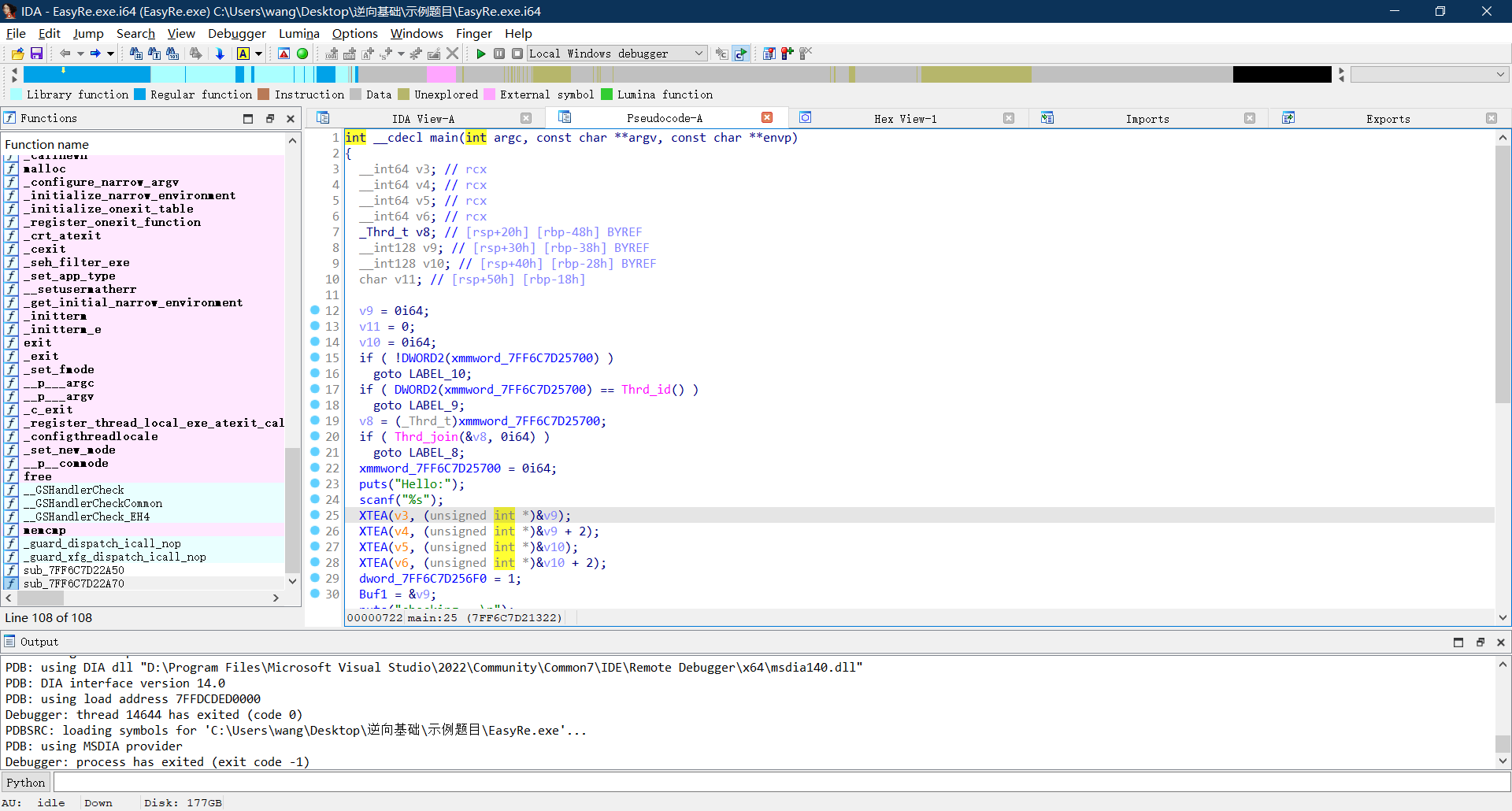
在imports里面找到了memcmp函数,然后在左边搜索,定位到密文比较的地方
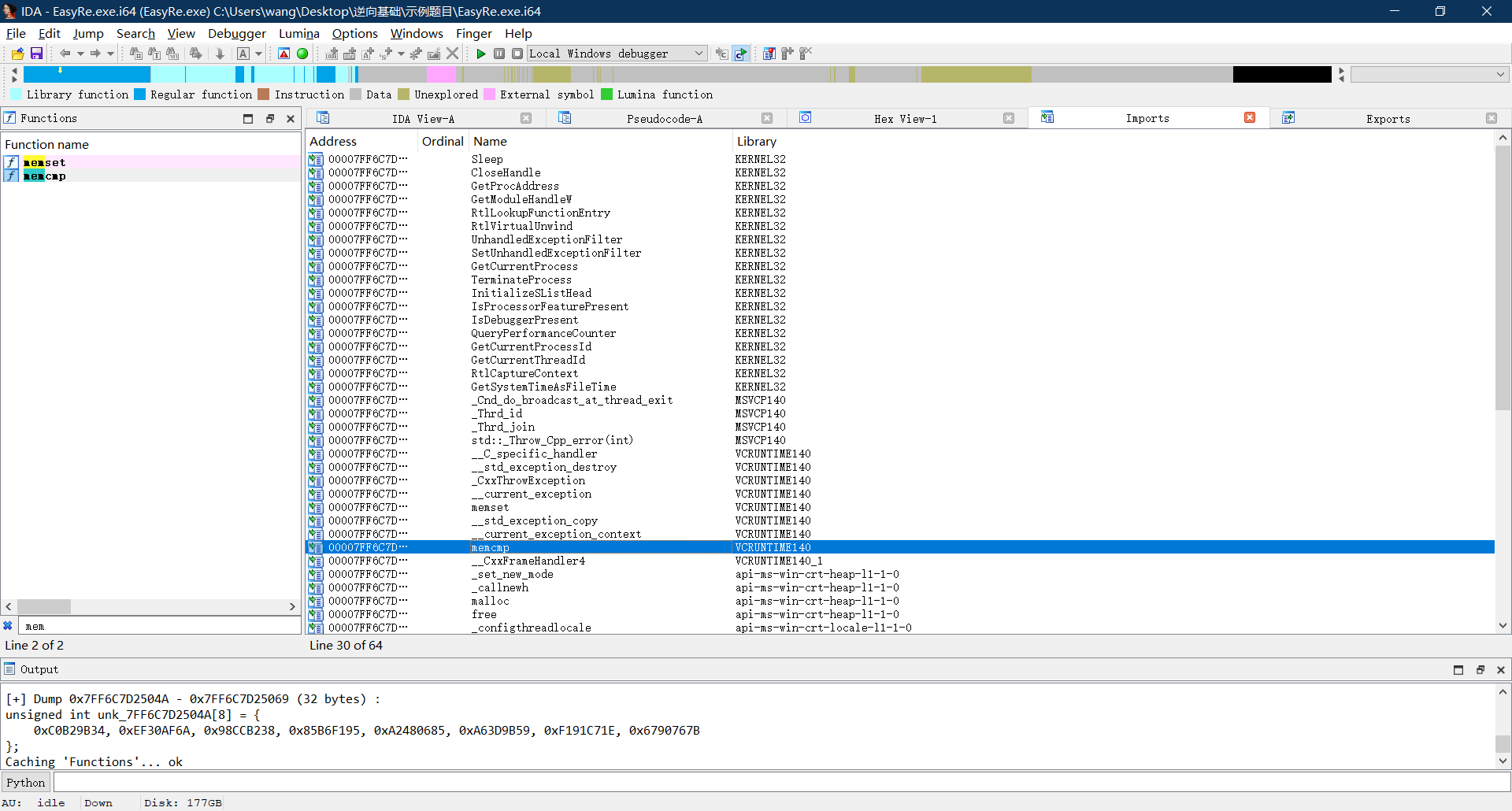
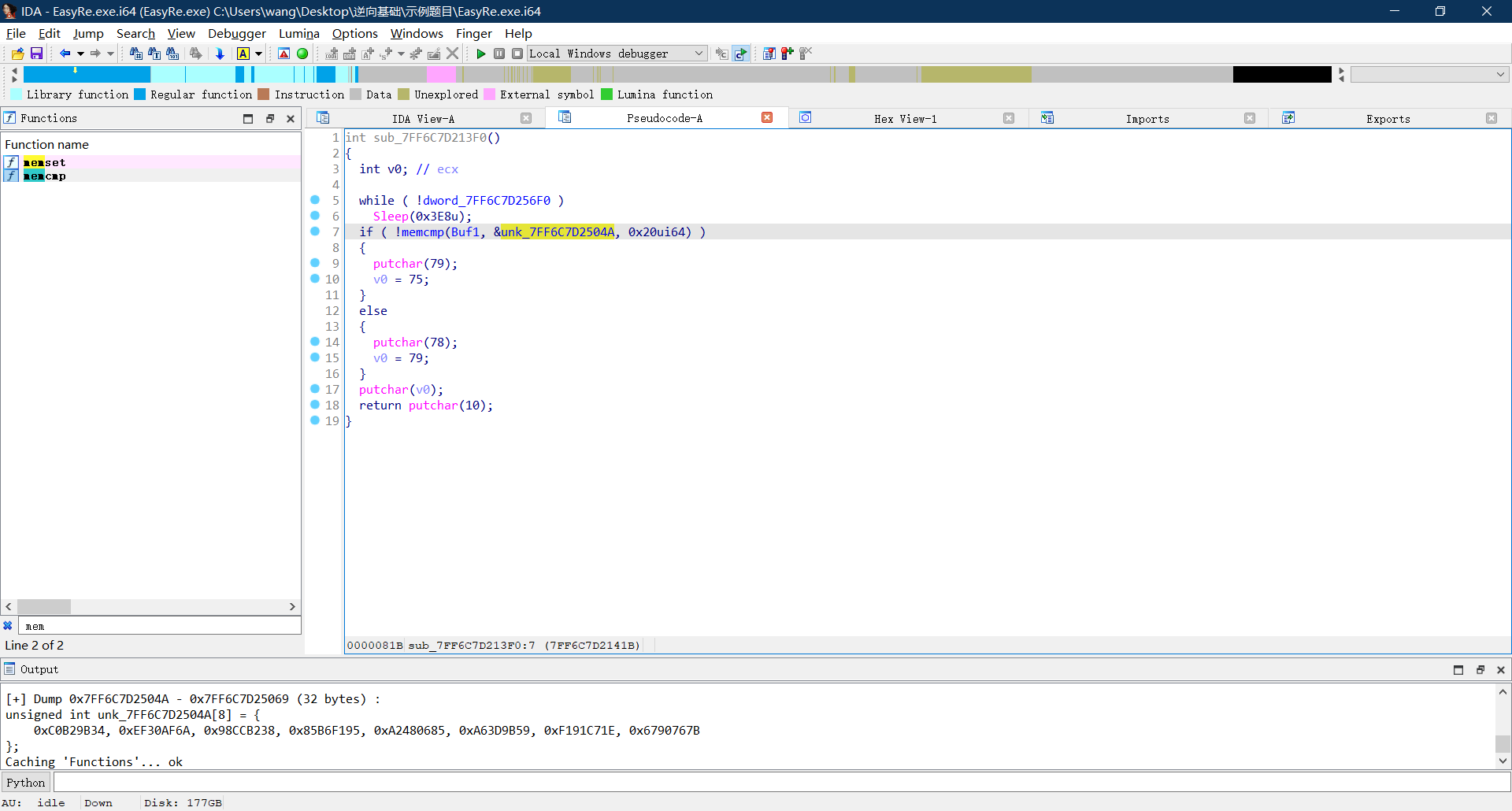
由于是调用了4次XTEA函数加密,XTEA每次是两组数据进行轮换加密,所以在这里是DWORD类型,得到下面的八组数据
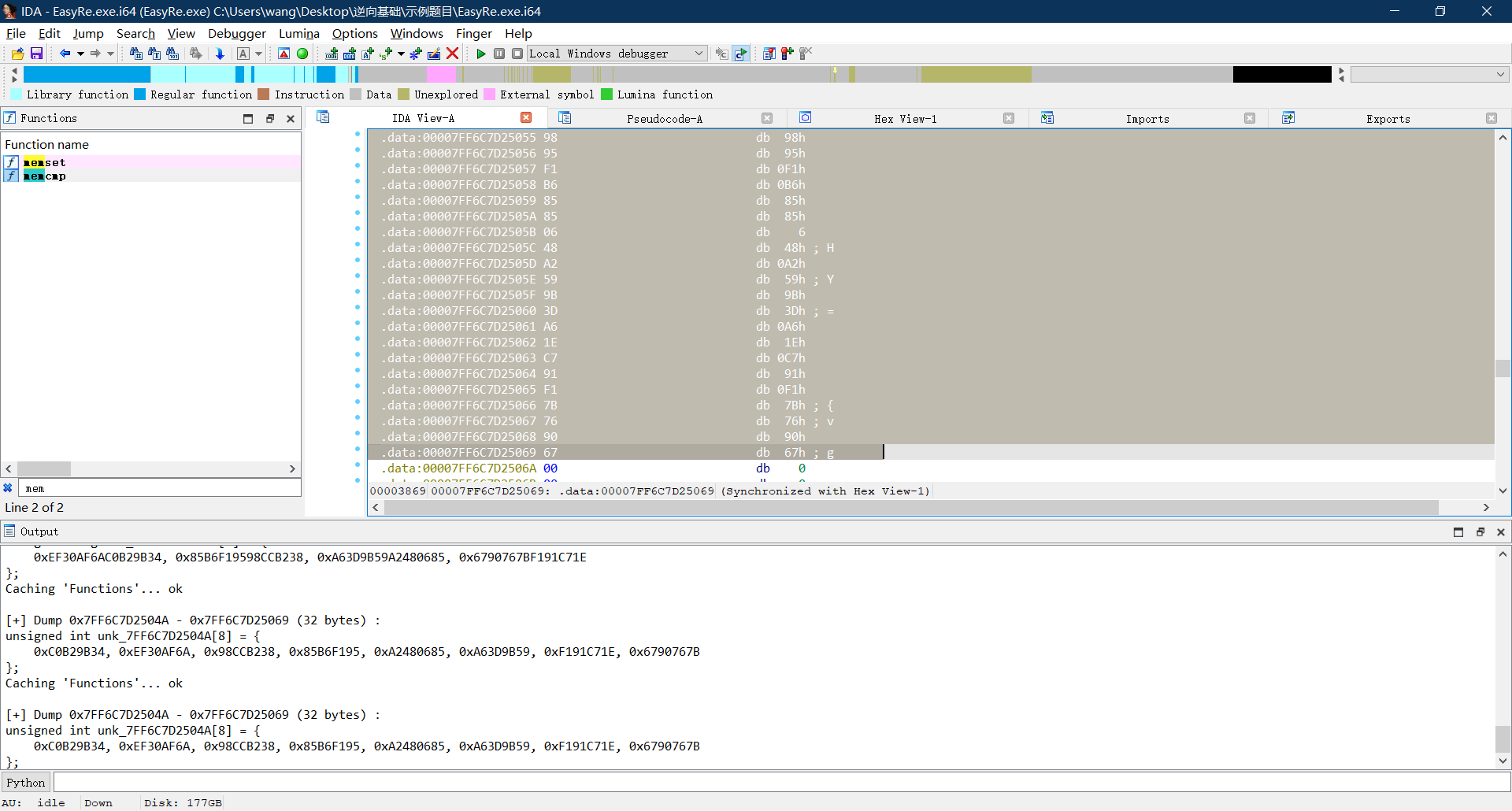
找到了密文,接下来就是寻找密钥
IDA动态调试
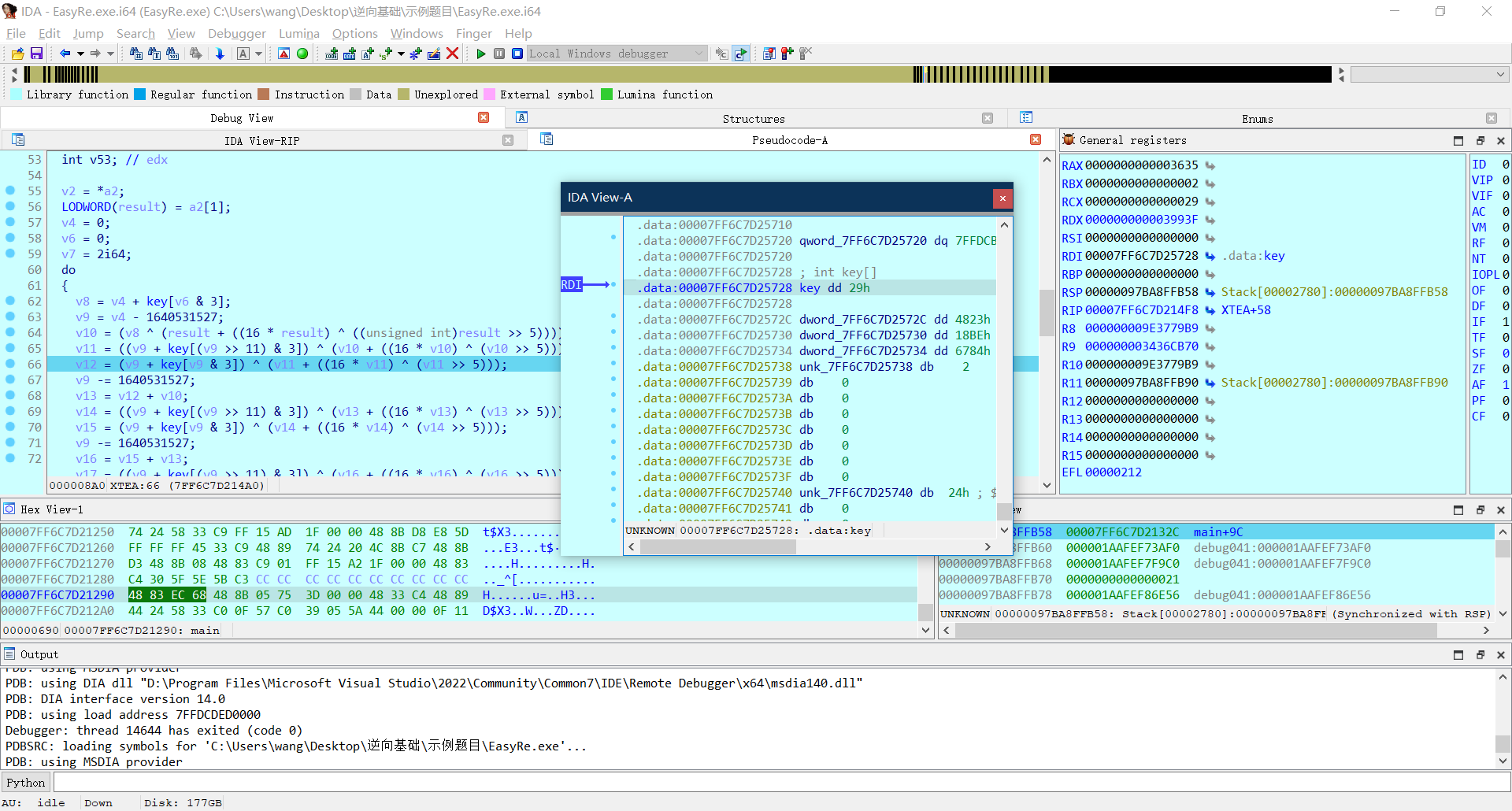
可以得到key
1
| uint32_t key[4] = { 0x29, 0x4823, 0x18BE, 0x6784 };
|
由于这个XTEA只是内层循环拆开了,所以实际上应该并没有什么魔改
直接上脚本尝试
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| #include <stdio.h>
#include <stdint.h>
void decrypt(unsigned int num_rounds, uint32_t v[2], uint32_t key[4]) {
uint32_t v0 = v[0], v1 = v[1], delta = 0x9E3779B9, sum = delta * num_rounds;
for (int i = 0; i < num_rounds; i++) {
v1 -= (((v0 << 4) ^ (v0 >> 5)) + v0) ^ (sum + key[(sum >> 11) & 3]);
sum -= delta;
v0 -= (((v1 << 4) ^ (v1 >> 5)) + v1) ^ (sum + key[sum & 3]);
}
v[0] = v0;
v[1] = v1;
}
int main(void) {
uint32_t unk_7FF6C7D2504A[8] = {
0xC0B29B34, 0xEF30AF6A, 0x98CCB238, 0x85B6F195, 0xA2480685, 0xA63D9B59, 0xF191C71E, 0x6790767B
};
uint32_t key[4] = { 0x29, 0x4823, 0x18BE, 0x6784 };
unsigned int r = 32;
for (size_t i = 0; i < 8; i += 2)
{
decrypt(r, unk_7FF6C7D2504A + i , key);
}
for (int i = 0; i < 32; i++) {
printf("%c", *((unsigned char*)unk_7FF6C7D2504A + i));
}
return 0;
}
|
然后检查
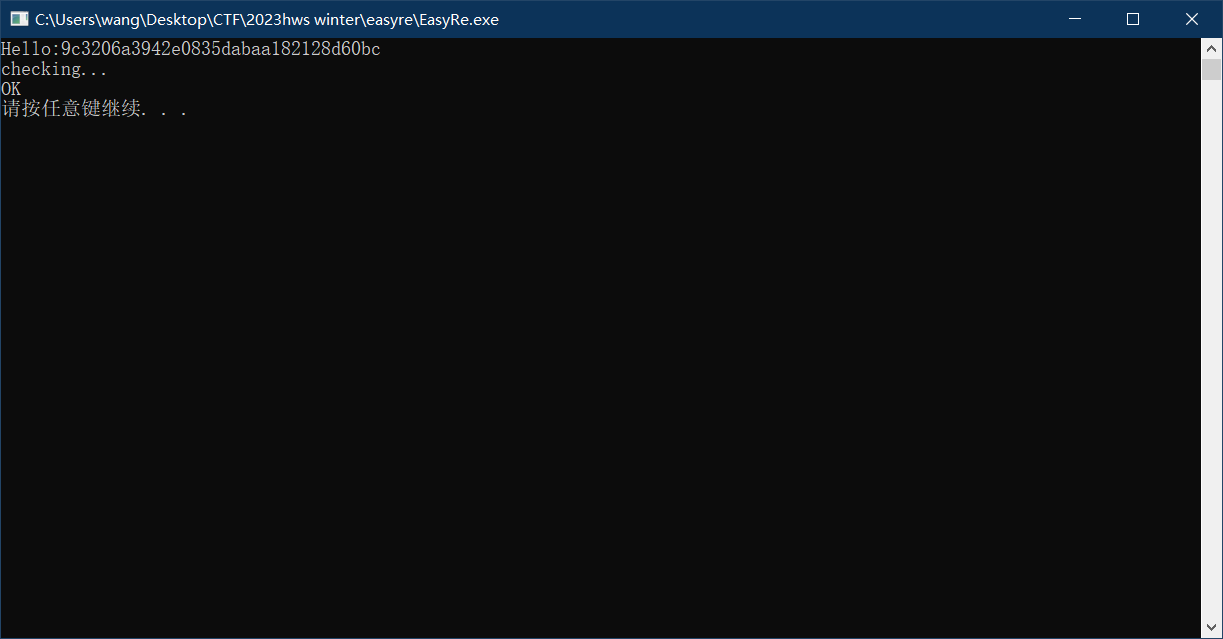
所以得到flag{9c3206a3942e0835dabaa182128d60bc}

















