2022 美团 MT-CTF Small 借鉴:[原创]2022MT-CTF Re-茶余饭后-看雪论坛-安全社区|安全招聘|bbs.pediy.com
在做题的时候看到是ELF文件,直接尝试在Ubuntu上面运行,但是提示段错误。然后用IDA64打开,一直报错。想怎么修复ELF头,让他能直接运行,也有大佬提示试试看是不是shellcode,但是都失败了,看到了wp人都傻了。
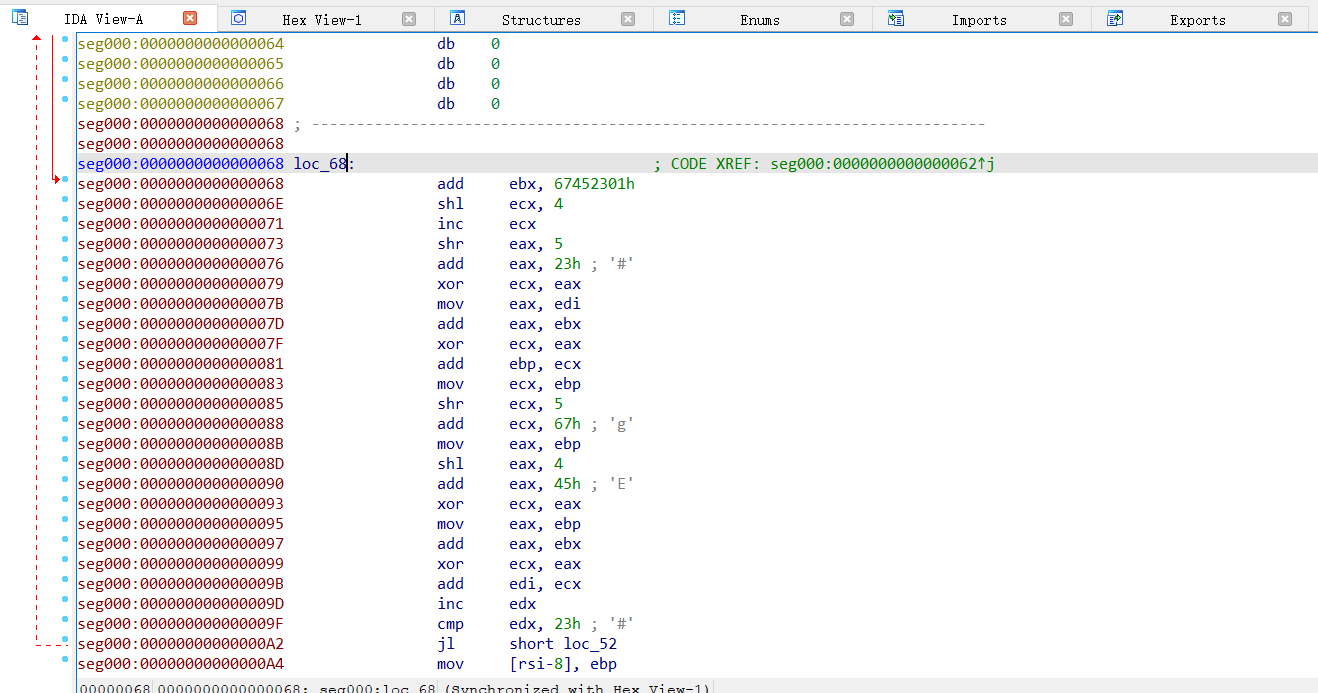
首先用IDA64, 二进制模式打开
然后在0x68处按C反汇编,
经典的三个数两次异或运算,左移4,右移5
看cutter的反编译更清楚,可以得知这是一个TEA加密
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 #include <stdint.h> int64_t entry0 (int64_t arg_10h, int64_t arg4, int64_t arg1) {0 ;0x3e0002 ;4 ;if (*(rsp) != 2 ) {goto label_1;4 ;do {0x67452301 ; 4 ; 5 ; 0x23 ;5 ; 0x67 ;4 ; 0x45 ;while (edx < 0x23 ); 8 )) = ebp;4 )) = edi;0x20 ;if (esi < ecx) {goto label_0;0x20 ;do {if (*((esi + 0x100f7 )) != cl) { goto label_1;while (esi != 0 );1 ;0x100f3 ;1 ;4 ;0x3c ;"outsd dx, dword [esi]" );"outsd dx, dword [rsi]" );if (esi overflow 0 ) {0 ], fp_stack[0 ]);0 ] *= *((rbp + rdx*8 - 0x62 ));"insd dword [rdi], dx" );"out 0x4e, eax" );return void (*0x10180 )() ();
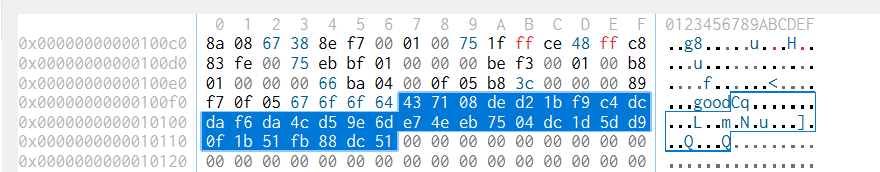
直接定位到0x100f7,可以找到密文就是在0x100f7~0x100f7+0x20之间
解密脚本
1 2 3 4 5 6 7 8 enc=list (bytes .fromhex('437108ded21bf9c4dcdaf6da4cd59e6de74eeb7504dc1d5dd90f1b51fb88dc51' ))for i in range (0 ,len (enc),4 ):0 for j in range (4 ):8 *j))print (hex (num),end=',' )
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 #include <iostream> #define ut32 unsigned int #define delta 0x67452301 void Tea_Decrypt (ut32* enc) {unsigned int sum = 0x67452301 * 0x23 ;0 ];1 ];for (int i = 0 ; i < 0x23 ; i++) {4 ) + 0x45 ) ^ (v0 + sum) ^ ((v0 >> 5 ) + 0x67 );4 ) + 1 ) ^ (v1 + sum) ^ ((v1 >> 5 ) + 0x23 );0x67452301 ;0 ] = v0;1 ] = v1;void Tea_Encrypt (ut32* src) {0 ;0 ];1 ];for (int i = 0 ; i < 0x23 ; i++) {0x67452301 ;4 ) +1 ) ^ (v1 + sum) ^ ((v1 >> 5 ) + 0x23 );4 ) + 0x45 ) ^ (v0 + sum) ^ ((v0 >> 5 ) + 0x67 );printf ("%08x\n" , sum);0 ] = v0;1 ] = v1;int main () {8 ] = { 0xde087143 ,0xc4f91bd2 ,0xdaf6dadc ,0x6d9ed54c ,0x75eb4ee7 ,0x5d1ddc04 ,0x511b0fd9 ,0x51dc88fb };for (int i = 0 ; i < 8 ; i += 2 ) {for (int i = 0 ; i < 32 ; i++) {printf ("%c" ,*((unsigned char *)enc+i));return 0 ;